MODULE 6

LOAD MANAGEMENT
Metaframe XPa or XPe product license be installed and actived.
Server calculated its load and sends values for all possible load evaluation
criteria to the data collector in the zone.
The data collector forwards the request of the published application to the
least busy server in the farm ,if all servers are at maximum load ,the request
is denied.
The routing of ICA connections to Metaframe XP servers occurs during the initial
access to the application.
Load management is not fault tolerant ,no dynamic rebalancing of active ICA
connections if the server hosting application goes down.
LOAD EVALUATORS
Servers and published application can have a specific load evaluators
attached to it.
Are rules (identifier,description,thresold settings that can be adjusted)
to balance the load in a server farm.
One or more rules can be used in a load evaluators and those work together.
To create ,customize ,duplicate ,attach and delete Load Evaluators use CMC's
Load Evaluators node.
Xp come with two preconfigured load evaluators :
-
default : use the rule SERVER USER LOAD
(full load when user sessions exceed 100),is automatically attached a server
in the farm with xpa or xpe license.
Work best on 4-way server with 2Gb to 4Gb of ram an two raid controllers.Cannot
be modified.
A load evaluator is always attached to a server running XPa or XPe.
-
advanced : rules CPU utilization(full load
processor time over 90% no load under 10%) ,memory usage(full load memory
usage over 90% no load under 10%) ,page swap (full load page swap over 100
no load equal to 0).
Work best on a single CPU, Pentium 400MHz nsystem with 192MB of RAM and
a SCSI Ultra Wide Controller
Cannot be modified ,create copy and change the settings.
Load evaluators can be attached to servers in the server farm.
By default, the Default Load Evaluator is attached all servers.
Its recommended that all the servers in the farm use the same load ev.
Thresold never set to the maximum value.
A serve can become overloaded if all servers in the farm are close to being
fully loaded and new connections are coming in faster than the data store
can update.
Default no load evaluators are attached to the applications.
An application can be published across multiple servers but the application
will not be load balanced across the servers unless a xpa or xpe license is
used.
Load ev. attached to applications will not be used to balance user load in
mixed mode.
Most load balancing needs can be accomplished by attaching load evaluators
to servers.Attaching load evaluators to published applications increases the
load on the data collector in a zone, and consume reosurces and slow performance.
The following rules are available :
| RULE |
EXPLANATION |
| Application User Load |
By default, reports full load whne thr number of users is greater than
100.
N.B.: in mixed mode this rules don't work, only with XPa and XPe. |
| Context Switches |
By default, reports a full load when the number of context switches
per second is greater than 16.000.
Reports no load when the number of context switches per second is less
than 900. |
| CPU Utilization |
By default, reports a full load when processor utilization is greater
than 90% and no load when the processor utilization is less than 10%.
This rule is based on a scale of 100. |
| Disk Data I/O |
By default, reports a full load when the total disk I/O in KB per second
is greater than 32,767 and no load when the total disk I/O in KB per second
is equalto 0.
N.B.: if windows NT server 4.0 TS with SP6 is being run, disk perf -y
must also be run on the server when using this rule. |
| Disk Operations |
By default, reports a full load when the total disk operations (read/writes
per second) are greater then 100 and no load when are equal to 0.
N.B.: if windows NT server 4.0 TS with SP6 is being run, disk perf -y
must also be run on the server when using this rule. |
| Ip Range |
Allows or refuses access to a published applications based on whether
the IP address of the ICA client is within the specified IP address range.
If Nfuse is being used to access, the rule will be ignored unless client
enumerations are allowed with Nfuse.
N.B.: only IP addresses are supported all other protocols are ignored.In
mixed mode ICA client can connect even though their IP addresses are in
the denied range. |
| License Threshold |
By default, reports a full load when the number of assigned licenses
in use on the server is greater than 10 or the number of pooled licenses
in use on the server (not server farm) is greater than 50.
N.B.:in mixed mode the rule can redirect ICA clients to different subnets
when XP licenses are exhausted. |
| Memory Usage |
By default, reports a full load when memory usage is greater than 90%
adn no load when is less than 10%. |
| Page Fault |
By default, reports a full load when the number of page faults per second
is greater than 2.000 and no load when is equal to zero. |
| Page Swap |
By default, reports a full load when the number of page swaps per second
is greater than 100 and no load when the number is zero. |
| Scheduling |
Allows or denies access to servers or published applications during
certain hours. |
| Server User Load |
By default, reports a full load when the number of users on a server
is greater than 100.
N.B.: this is the only rule that should be used in mixed mode. |
Administrator can change the values associated with the above
rules to achieve the desired output for the load evaluator.
The load manager monitor can assist in fine tuning the rule settings and combinations
needed to achieve the desired load management criteria.
Load Manager Monitor
Allows an administrator to view the activity
of rules attached to a server.
To display it, right click a server and then click Load Manager Monitor.
A load evaluator beginsevaluating the load as soon as it is attached to a
server or published application.
ENCRYPTION
Encryption process transforms data into a form that is unreadeble by anyone
without a unique bit of information called key.
Two types on encryption algorithms are :
- Symmetric Key Algorythms : use same key to encrypt and
decrypt the encoded data.
Advantage is the speed ,disavantage is that the secret key used to encrypt
the data must be sent to those needing to decrypt the data.
- Public-private Key Algorythms : rely on mathematical properties
to create a set of keys ,with one key to encrypt the data and another key
to decrypt the data.
The encrypt-only key is called a PUBLIC KEY.
The decrypt-only key is called a PRIVATE KEY.
The public key can be transmitted without problems because knowing the public
key does not aid anyone in decrypting the encrypted data.
ENCRYPTION STRENGTH AND PERFORMANCE
The strength of encryption algoryth depends on two factors : the strength of
the algorythm itself and the size of the key used with the algorithm.
Tryig every possible key is known as a brute force attack.
A key eight bits long contains 256 possible keys.
A 56-bit key contains 2^56 possible keys.
RC5 AND DIFFIE-HELLMAN
RC5 used to encrypt ICA packets in metaframe XP.
Is a block cipher ,where a block use a variable size key combined with the encrypted
version of the previous block to encrypt the current block.
Rounds are the number of times each block is passed through the encryption algorythm
,XP uses a 64-bit block size with 12 rounds and 40,56, or 128 bit key size.
RC5 is a symmetric key algorythm.
In the RC5 algorythm the key must be exchanged ,The Diffie-Hellman
Key Agreement Algorythm does this by generating the same secret key on the ICA
client and XP server without transmitting info ,which could compromise the security
of the key.
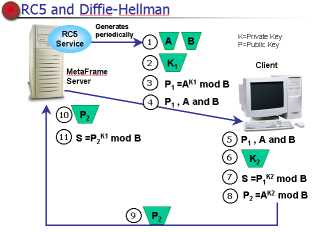
SECURITY WITHIN METAFRAME XP
XP contains security features that allow ICA clients to connect to metaframe
servers over secure communication channels.
XP uses both a symmetric key and public-private key algorythm in its security
: RC5 encrypt and decrypt the data ,Diffie- Helmann generates the secret keys.
Xp offers the following security features :
- 128-bit encryption during user authentication;
- basic ,40 ,56 and 128 bit encryption levels for ICA sessions;
- configurable encryption levels that can be assigned to ICA connections.ICA
clients that don't meet the minumum level of encryption will not be able to
use the ICA connection;
- configurable encryption levels that can be assigned to published applications.ICA
clients that don't meet the minumum level of encryption will not be able to
use the published application.
- compatibility with the latest ICA clients DOS ,win16 ,win32 and web clients
,linux86 ,winCE and all secure ica clients;
- dynamic key generation for each connection.A system service periodically
generates new Diffie-Hellman parameters in the background.
All ICA commands and data are encrypted ,including : keystrokes ,mouse data
,graphic information ,client drive data ,client printer data ,client audio data.
SECURITY AND NFUSE
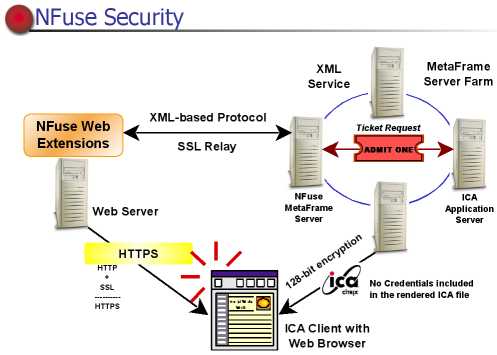
The security algorythm can also used when Nfuse delivers application sets to
users.
SSL relay feature included with metaframe can protect the info when being transferred
between the web server and the XP server.
The security components in XP offer protection for data transfers during :
- th elionk between the ica client and the xp server is safeguarded with RC5
encryption ,as well as time-sensitive user authentication tickets.
- the procurement of application set from the XP server farm to the web server.
XML service must be installed on at least one XP server ;Nfuse uses XML to
trnasmit data between web server and the designeted XP server in the farm.
The user credentials and application data are sent as clear text between web
server and XP server unless SSL is used to encrypt the info.
The following mechanisms ensure safe user credentials and application data
transmission over each connection when using Nfuse :
- SSL relay uses the Secure Socket Layer protocol to secure the comunications
between XP server and web server.
SSL don't need when Nfuse is installed onthe same server as IIS.
- Secure Hypertext Transfer Protocol (HTTPS) is a secure version of HTTP used
on hte web. It uses the SSL protocol to provide security ,without https the
link is not secure.
- RC5 provides protection for data being sent ICA client and XP server.
- User Authentication Ticket is a unique key assigned to user ,used to identify
the sender of the message and reduce security risks logons and provides security
for ICA files.
- If user authentication tickets will be used the XML service must be
installed on every server XP in the farm.
- If user authentication tickets will not be used ,the XML service only
needs to be installed on one Xp server in the farm.
CITRIX SSL RELAY CONFIGURATION
Citrix SSL relay decrypts the data sent between the two servers.
SOCKSv5 is used to redirect the data to the XML service.
The citrix SSL relay configuration tool can be used to configure the Citrix
SSL relay.
The tool has three tabs : RELAY CREDENTIALS(contains settings that configure
the server certificate for the SSL relay) ,CONNECTION(contains settings that
configure the listener prot and specify the destinations for the SSL relay)
,CIPHERSUITES(is an encryption/decryption algorythm).
FIREWALLS
Firewalls prohibit unauthorized clients from accessing the network
,IP addresses determine who is permitted or denied access.
On a citrix network without a firewall ,ICA client send requests to XP servers.
XP server returned the internal IP address of data collector for the zone
to the ICA client.
ICA client contact the data collector for a browse list or the internal IP
address of the least busy server offering an application.
When a firewall is added to a citrx network ,it must be configured to allow
TCP packets on port 1494.
ICA client uses UDP port 1604 or TCP 80 for browsing and 1494 toestablish
the ICA connection to servers.
Opening ports on a firewall causes security risks ,to increase a firewall's
security you can use a SOCKS proxy server or netowrk address translkation
(NAT).
SOCKS Proxy server
SOCKS proxy server allows controlled firewall traversal by limitng
access to XP servers.
Uses the SOCKS protocol to make requests on behalf if ICA clients attempting
to access a XP server.
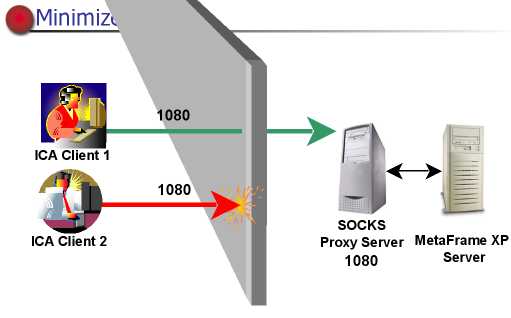
To protect XP servers install the SOCKS server between XP servers
and the firewall.
Pass only traffic that is directed to the socks proxy server and comes from
specific devices.
NAT
With NAT ,each internal XP server receives an alternate IP address
,only ICA client that know this IP address can get through the firewall.
By default ,all XP servers return the internal IP address of the data collector
in hte zone.
Assigning Alternate IP addresses : with the ALTADDR command
onthe xpserver.
For example to assign the alternate IP address 208.132.126.70 to a XP server
type : ALTADDR /set 208.132.126.70 at the server's command line.
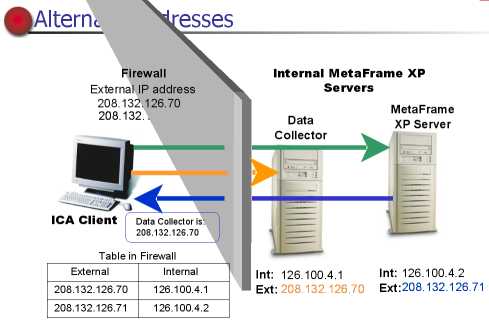
Network Address Translation Rules for the Firewall
For example (show image above) : an ica client sends a request
to an alternate external IP address ,208.132.126.71.
The firewall translates the IP address and sends the request to the server
with the internal IP address of 126.100.4.2.
The internal server sneds the alternate IP address of the data collector throught
the firewall to the ICA client.
Ica client contacts the data collector for the alternate IP address of the
least busy server in the network.
The data collector return the alternate IP address ,the ICA client contacts
the server and the application begins.
Failures
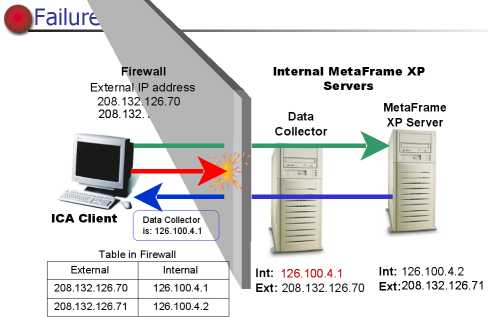
If the server return the internal ip address to the ica client
and attempting to contact ,the firewall does not recognize the address and
rejects the request.
Requesting Alternate IP Addresses
An administrator can configure an ICA client to request the
alternate IP address of XP server.
A user can edit th eproperties of a specific application set or the Custom
ICA Connection folder within the Program Nighborhood and click the Properties
icon.
User can configure a ucstom ICA connection to go a particular XP server directly
rather than load balancing the ICA connection ,by entering the alternate IP
address of the data collector.
When load balancing is used on XP server farm ,the data collector in the zone
returns the alternate IP address and port number of the least busy server
to the external ICA client using TCP port 1494.
The ICA client uses the alternate IP address to connect to the server whose
alternate IP address was returned by the data collector.
Specifying a Different TCP/IP Port
It is possible to change the TCP/IP port used by the ica protocol.
Choose any port number in the range of 0-65535 as long as it does not conflict
with other reserved ports.
To change TCP/IP port type ICAPORT /port:xxxx on each server in the subnet.
The new TCP/IP port number must be configured in each ICA client.





